4 Easy Facts About Aws S3 Backup Shown
Not known Incorrect Statements About Aws S3 Backup
Table of ContentsThe Ultimate Guide To S3 BackupOur Data Protection PDFsS3 Backup Can Be Fun For AnyoneFascination About Aws Backup
energies that allow you to monitor and also filter network web traffic. You can make use of firewalls to make sure that only accredited individuals are allowed to accessibility or transfer data. controls that assist you confirm credentials and guarantee that customer privileges are applied properly. These steps are normally made use of as component of an identification and also accessibility administration (IAM) remedy and in mix with role-based access controls (RBAC).File encryption protects your data from unauthorized gain access to also if data is taken by making it unreadable. Endpoint security software program usually enables you to check your network boundary and also to filter website traffic as needed.
This can be done after information is processed and assessed or regularly when information is no more appropriate. Eliminating unneeded information is a demand of numerous compliance laws, such as GDPR. For more information regarding GDPR, take a look at our guide: GDPR Data Defense. a set of practices and also innovations that establish just how a company handles a calamity, such as a cyber assault, all-natural calamity, or massive devices failure.
How Aws Cloud Backup can Save You Time, Stress, and Money.

If you collect even more than what you require, you increase your liability and can produce an undue burden on your security teams. Reducing your data collection can also aid you reduce transmission capacity and also storage space. One way of accomplishing this is to utilize "validate not store" frameworks. These systems make use of third-party information to confirm customers and eliminate the need to store or transfer customer data to your systems.
Mirroring this, GDPR has made user authorization a key element of information usage and also collection. Having clear individual notices describing when data is accumulated and why.
Extremely often, data portability implies the capability to relocate information in between on-premises data centers as well as the public cloud, and in between various cloud companies. Data mobility also has lawful implicationswhen data is stored in different countries, it is subject to different laws and also guidelines.
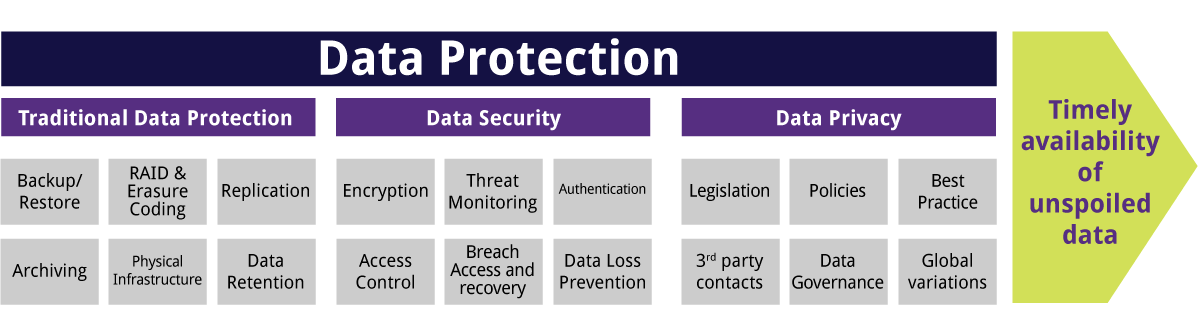
The Greatest Guide To Data Protection

This makes it hard to move information from one cloud to an additional, and also creates vendor secure. Progressively, companies are looking for standardized means of saving as well as managing data, to make it portable across clouds. Mobile phone protection refers index to steps developed to shield delicate information stored on laptop computers, mobile phones, tablets, wearables and various other mobile gadgets.
In the modern IT environment, this is an essential facet of network security. There are numerous mobile information protection devices, created to shield mobile gadgets and data by identifying risks, developing backups, as well as protecting against threats on the endpoint from reaching the business network. IT personnel use mobile data protection software program to allow safe mobile access to networks and systems.
Ransomware is a sort of malware that secures user data and also requires a ransom money in order to release it. Brand-new kinds of ransomware send out the information to enemies before securing it, permitting the enemies to obtain the organization, threatening to make its sensitive info public. Back-ups are a reliable protection against ransomwareif an organization has a current duplicate of its information, it can recover it as well as reclaim accessibility to the data.
The Definitive Guide for Data Protection
At this stage ransomware can contaminate any kind of linked system, consisting of backups. s3 cloud backup. When ransomware infects back-ups, it is "video game over" for data security approaches, since it comes to be impossible to restore the encrypted data. There are several strategies for protecting against ransomware and particularly, stopping it from infecting backups: The easiest method is to use the old 3-2-1 backup regulation, keeping 3 duplicates of the information on two storage space media, one of which is off facilities.
Storage space suppliers are using immutable storage, which ensures that data can not be changed after it is stored (https://www.goodreads.com/user/show/157987042-clumio). Big organizations have numerous datasets saved in various places, and also numerous of them may duplicate data in between them.
It is no usage protecting a dataset as well as ensuring it is compliant, when the data is copied in another unknown location. CDM is a kind of option that discovers duplicate information and also aids handle it, comparing similar data and allowing administrators to remove unused duplicates. Disaster recuperation as a service (DRaa, S) is a taken care of solution that provides a company a cloud-based remote calamity healing website.
With DRaa, S, any type of dimension company can reproduce its local systems to the cloud, as well as conveniently restore operations in case of a catastrophe. DRaa, S solutions utilize public cloud framework, making it feasible to store multiple copies of facilities and also data across several geographical areas, to increase resiliency. Data defense calls for effective storage space technology (https://about.me/clumi0).